Perfect Tips About How To Stop Port Scanning

Scan the ports that are.
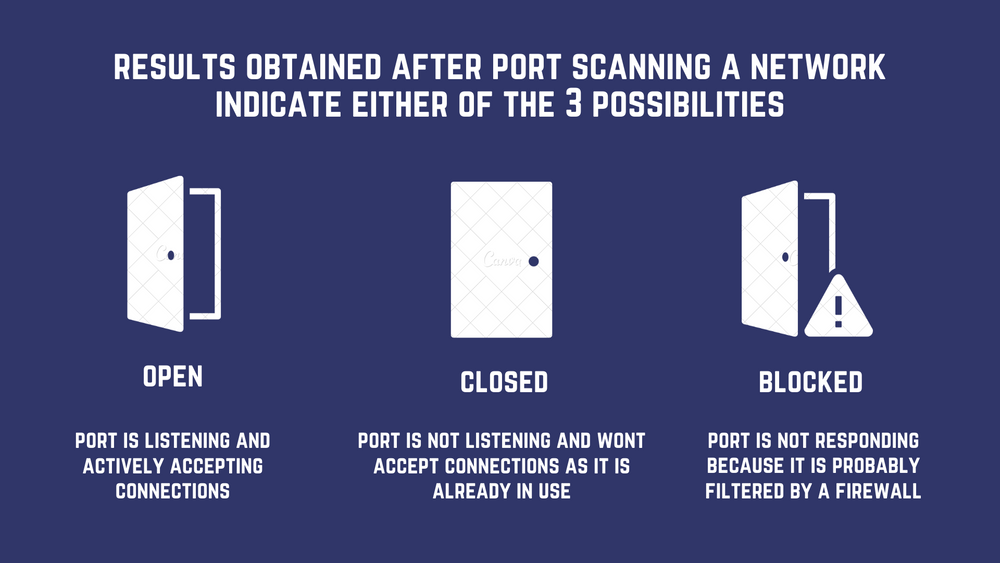
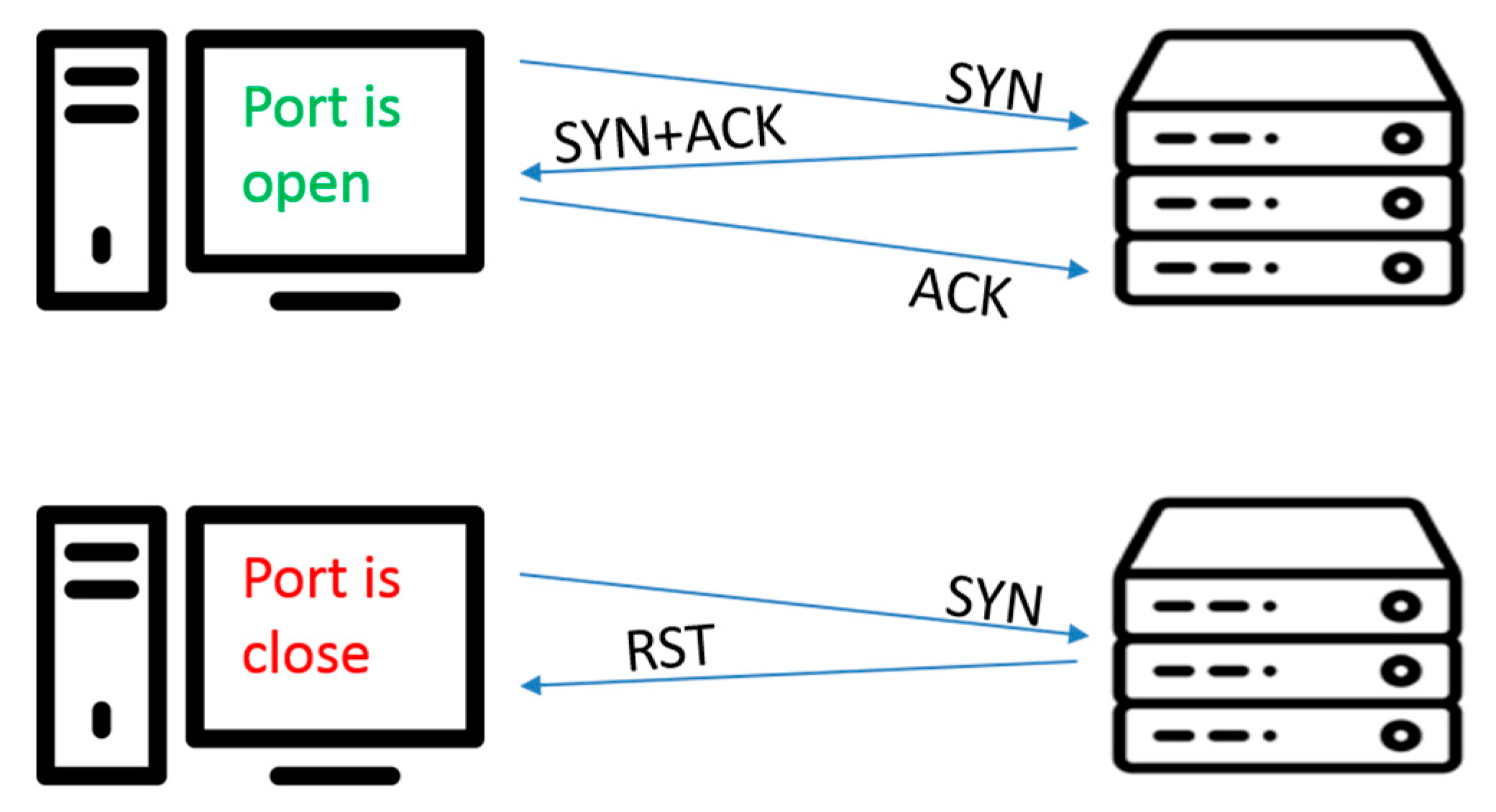
How to stop port scanning. We have fortigate in azure, we would like to prevent port scanning. The following sample code demonstrates how to prevent port scanning using stealth discards and silent drops. If a port is open, or listening, it will respond to the request.
Port scanners are valuable tools in. Scan the first 1000 ports on a cidr range. Port scanning is generally done in stages:
It can also be the precursor to an intrusion. The goal is to hide some ports like remote desktop on a different port. Example of rules to protect against nmap scans.
Move sensitive data and servers behind the network perimeter and control access with a vpn or other access control. I tried create ips policy and select port.scanning, but it. Is it possible and how i can do it?
Open ip> firewall select the “filter rules” tab and. There are two choices to protect a network from being scanned. In this section, we’ll create rules to filter and drop identified nmap scans.
Port scan is a technique hackers use to discover weak points in a network. Corporate firewalls can reply to a port scan in three ways: For this, we add a rule to detect the ips.
A closed port will respond with a. Discover port scanning techniques, the difference between port scanning vs. Network scanning, & how to prevent port checker attacks.
Console copy netsh wfp set options netevents=off disable. Port scanning can be the start of good network security. The first step in preventing malicious actors entering your network using a port scan attack is to run frequent port scans.
Scan the first 1000 udp ports on responding devices. By definition, port scanning is the process of connecting to ports and checking the response and any obvious methods of stopping port scanning will result. Learn how to identify and prevent unwanted port scans.
Disable wfp logging by running the following netsh command from an elevated command prompt: In this article, we explain what port scanning is, the different types of port scanning, and how to protect yourself from attackers using port scanning to gain. Do the port scan before the attacker: